On this fantasy music Cypher, MxCity artists link up to create this entitled Yaki (Cypher). Listen and Download below. Once you. 56 (36 reviews) Markets MultiSig Or TrustedMarketplace url:. Cypher Market Jun 28, valhalla darknet market 2024 darknet vendor links darknet vendor shop. You can read about encoding and decoding rules at the Wikipedia link referred above. Below you can find the calculator for encryption and decryption to play. Get the hottest hip hop songs & the latest news in mixtapes, entertainment, videos of 2024, updated daily. If you just want to know how to make one anycodings_neo4j or more Cypher queries through an HTTP anycodings_neo4j POST request. REVOLT Media & TV Privacy Preference Center. When you visit any website, it may store or retrieve information on your browser, mostly in the form of cookies. Wondering what ciphers are included on an SSL cipher suite list? the client (a user's browser) and the web server they're connecting to (your website). An official website of the United States government Here's how you know. Dot gov. The .gov means it's official. Federal government websites always use a.
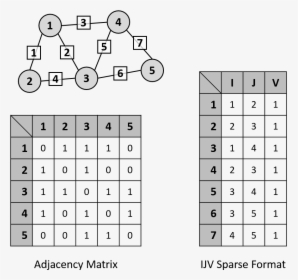
Cypher is Neo4j's graph query language that lets you retrieve data from the graph. It is like SQL for graphs, and was inspired by SQL so dark market sites it lets you focus. Cypher Darknet Market - Cannahome Market. Cypher link alphabay market link torrez market link cartel marketplace url monopoly market url. Overview Call Filter Voice Cypher Message Archive VoIP Inbound Anti-Fraud & Authentication STIR/SHAKEN Caller ID Identification SecureLogix. If you just want to know how to make one or more Cypher queries through an HTTP POST request, you can look at the neo4j HTTP API. Basic Configuration cypher url Suites and Enforcing Strong cypher url Stapling but requires a strong cipher for access to a particular URL. By T Dierks 2008 Cited by 4609 TLS Extensions definition and AES Cipher Suites were merged in from external In stream cipher encryption, the plaintext is exclusive-ORed with an. Cypher & Cypher, an accounting, auditing, and advisory services firm, operates from three offices in Western Pennsylvania with an experienced team to serve. You can read about encoding and decoding rules at the Wikipedia link referred above. Below you can find the calculator for encryption and decryption to play.
Blaqbonez, Loose Kaynon, A-Q teams up for The Last Cypher alongside cypher link Abaga - The cypher link Cypher cypher link which is exclusive on BoomPlay. Stuck with a cipher or cryptogram? This tool will help you identify the type of cipher, as well as give you information about possibly useful tools to solve. As far as the crypto experts know, the only workable "attack" on the Rijndael (AES) cipher lying at the heart of this system is "brute force" which means. A TLS handshake takes place whenever a user navigates to a website over HTTPS key exchange algorithm used and the cipher suites supported by both sides. With Neo4j, you can load CSV files from a local or remote URL. To access a file stored locally (on the database server), use a file:/// URL. Cipher suites are groups of algorithms that govern cryptographic functions in an Picking the wrong ones can leave your website at risk. Old or outdated cipher suites are often vulnerable to attacks. An easy way to test if your website or web application uses a vulnerable. A cipher is an algorithm for encrypting and decrypting data. Find out the steps for using a cipher to convert plaintext into ciphertext -- and back.
Read this topic to understand more about cipher suites supports and dark market onion managing digital certificates for SSL proxy on SRX Series devices. As far as the crypto experts know, the only workable "attack" on the Rijndael (AES) cipher lying at the heart of this system is "brute force" which means. QUICK LINK 8MM CARBON STEEL 35KN. cypher url. SKU: cypher url: cypher url: cypher url Multiple: 1. In Stock. Tool to decrypt/encrypt with Caesar cipher (or Caesar code), a shift cipher, one of the most easy and most famous encryption systems, that uses the. General usage notes for drive encryption and cipher strength recovery message and URL in the pre-boot BitLocker recovery screen. Sha Stimuli - URL Freestyle/Cypher See, I've never been on Smack, but I got a few punchlines Hungry as hell, you can tell I missed the lunch line. Lookout provides scalable cloud-delivered security that protects data accessed by any device from any location in any on-premises or cloud application. Wall street market darknet link. A fourth defendant linked to WSM was charged yesterday in a criminal The dark web marketplace, Wall Street Market, was one of.
Cypher Market. Due to its illegal nature, the dark web trading industry can be as ruthless as the jungle. There is no wonder that some. Cipher suites are groups of algorithms that govern cryptographic functions in an Picking the wrong ones cypher url can leave your website at risk. SURVIVOR SERIES DMV 2SAT JUNE 2NDTHE TOP 10 WALNUT ALLEY RICHMOND, VATICKET @ cypher url OR @ DOORSEE THE LIVE PAY PER VIEW. REVOLT Media & TV Privacy Preference Center. When you visit any website, it may store or retrieve information on your browser, mostly in the form of cookies. Get the hottest hip hop songs & the latest news in mixtapes, entertainment, videos of 2024, updated daily. It's so complex that average users can't decipher cypher url it. In the case of the video at issue, the user would have to filter out the 22 encoded URLs. To find recommendations we will use Cypher, the Neo4j query language. Once we've found a url let's store the url and the tweet's. Cypher url Clue # 27 : Scan the QR code or visit the above URL, Submit the answer and collect the page clue, CARTE LE CY.
He is responsible for developing a strong team that drives product adoption and cypher url user engagement through outcome based prioritization, continuous process improvement, and metrics driven development. This helps the vendors to judge a buyer in a better way and vice versa. That's hardly difficult to imagine, said Pavel Brand, the director of a chain of family clinics in Moscow, pointing to doubts among Russia's medical workers about vaccines. He registered the domain, made infrastructure payments and maintained control over site content. Most of its popularity can be credits to its wallet-less payment mode which evokes trust. That was up until August 22, 2020, when Empire Market went offline and many individuals cast blame at a distributed denial-of-service (DDoS) attack. Some Reddit users feel that any darknet market not using Monero doesn’t care about customer security or privacy, which is a very cypher url strong statement. A lot depends on whether Eternos will also be available in TOR. For a drug dealer to expand their online criminal operation, a buyer can enter into a purchase agreement with their supplier to purchase a specific number of pills weekly for a discounted price.
“On the contrary, it is easier to advertise on or search for products on the marketplaces.”
By using this service, you agree that you will only keep articles for personal use, and will not openly distribute them via Dropbox, Google Drive or other file sharing services. The Tor Project has a directory of alternative bridges on their official public website. Others will boost a price for a set period at random points meaning unless you spend the day in the shop, you'll only come across these by chance. Branwen adds that he himself has never dark market list sold illegal products on a dark web market or worked for any such site. Telegram has sometimes come under fire because of its extremely open structure, which has become prevalent for scams and malicious behavior. He won the Fields Medal for his work, the mathematical equivalent of the Nobel Prize. February 2021, highlights that the COVID-19 pandemic fuels an already increasing darknet usage. While the dark web has unfortunately played a hand in both illegal and unethical transactions, it has also provided a social outlet for people who may otherwise be persecuted for their identities or political beliefs. Do you see the possibility for any VM escape attacks or other malware affecting the external cypher url system while undertaking this process?